ModSecurity is a supporting module inside Apache web server,
which scans the incoming HTTP requests against some common web application attacks, e.g. SQL injection, XSS attacks, etc.
Notes: although the network of Website Solution equips with Snort NIDS (Network Intrusion and Detection System) and ModSecurity web application firewall, which provide added layers of security,
However, these modules cannot provide defense against all kind of attacks. Customer shall not see them as 100% secure.
For enhanced security, customer shall regularly update his/her own website PHP/MySQL application (e.g. WordPress, Joomla, OpenCart, Magento, PrestaShop, etc) to minimize the security threats.
No computer system can provide absolute security under all conditions.
We reserve the rights to add/amend/remove these value-added components.
In few circumstance, CMS/HTML editors may hit ModSecurity rules (especially those XSS related rules).
Users may temporarily disable ModSecurity engine, continue the work, and re-enable ModSecurity engine.
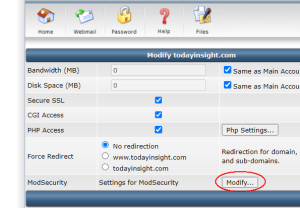
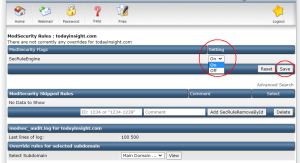
Modify ModSecurity
Turn SecRuleEngine off or on, and save it.
Wait for around 1 – 2 minutes, it will become effective.
After your work, it’d highly recommended to re-enable ModSecurity for enhanced security.
If it is some self-developed code, it is recommended that you put the code for the management page in (for example) /admin/ folder,
Then, you can add password-protected-directory onto the folder, and we can set ModSecurity to exclude this folder.
WordPress ChangeLog:
http://codex.wordpress.org/WordPress_Versions
Joomla ChangeLog:
http://developer.joomla.org/development-status.html
OpenCart ChangeLog:
http://www.opencart.com/?route=download/download
Magento ChangeLog:
http://www.magentocommerce.com/download/release_notes
PrestaShop ChangeLog:
http://www.prestashop.com/en/developers-versions